Two chips to authenticate each other
Chip-processing method could assist cryptography schemes to keep data secure
By Adam Zewe
By enabling two chips to authenticate each other using a shared fingerprint, this technique can improve privacy and energy efficiency.
Just like each person has unique fingerprints, every CMOS chip has a distinctive “fingerprint” caused by tiny, random manufacturing variations. Engineers can leverage this unforgeable ID for authentication, to safeguard a device from attackers trying to steal private data.
But these cryptographic schemes typically require secret information about a chip’s fingerprint to be stored on a third-party server. This creates security vulnerabilities and requires additional memory and computation.
To overcome this limitation, MIT engineers developed a manufacturing method that enables secure, fingerprint-based authentication, without the need to store secret information outside the chip.
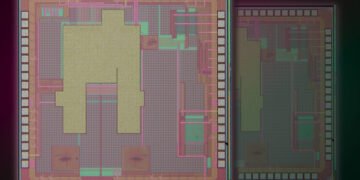
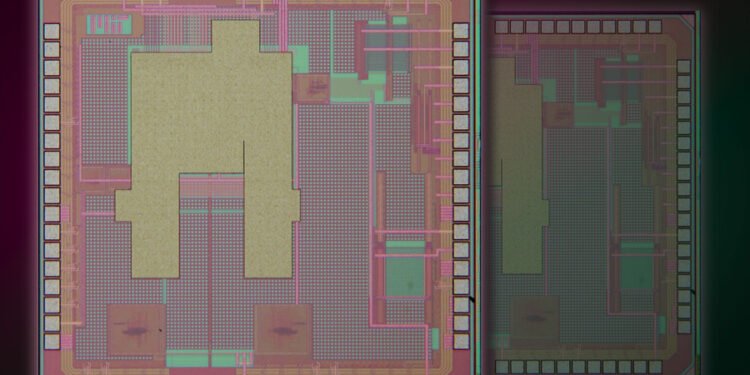
They split a specially designed chip during fabrication in such a way that each half has an identical, shared fingerprint that is unique to these two chips. Each chip can be used to directly authenticate the other. This low-cost fingerprint fabrication method is compatible with standard CMOS foundry processes and requires no special materials.
The technique could be useful in power-constrained electronic systems with non-interchangeable device pairs, like an ingestible sensor pill and its paired wearable patch that monitor gastrointestinal health conditions. Using a shared fingerprint, the pill and patch can authenticate each other without a device in between to mediate.
“The biggest advantage of this security method is that we don’t need to store any information. All the secrets will always remain safe inside the silicon. This can give a higher level of security. As long as you have this digital key, you can always unlock the door,” says Eunseok Lee, an electrical engineering and computer science (EECS) graduate student and lead author of a paper on this security method.
Lee is joined on the paper by EECS graduate students Jaehong Jung and Maitreyi Ashok; as well as co-senior authors Anantha Chandrakasan, MIT provost and the Vannevar Bush Professor of Electrical Engineering and Computer Science, and Ruonan Han, a professor of EECS and a member of the MIT Research Laboratory of Electronics. The research was recently presented at the IEEE International Solid-States Circuits Conference.
“Creation of shared encryption keys in trusted semiconductor foundries could help break the tradeoffs between being more secure and more convenient to use for protection of data transmission,” Han says. “This work, which is digital-based, is still a preliminary trial in this direction; we are exploring how more complex, analog-based secrecy can be duplicated — and only duplicated once.”
Leveraging variations
Even though they are intended to be identical, each CMOS chip is slightly different due to unavoidable microscopic variations during fabrication. These randomizations give each chip a unique identifier, known as a physical unclonable function (PUF), that is nearly impossible to replicate.
A chip’s PUF can be used to provide security just like the human fingerprint identification system on a laptop or door panel.
For authentication, a server sends a request to the device, which responds with a secret key based on its unique physical structure. If the key matches an expected value, the server authenticates the device.
But the PUF authentication data must be registered and stored in a server for access later, creating a potential security vulnerability.
“If we don’t need to store information on these unique randomizations, then the PUF becomes even more secure,” Lee says.
The researchers wanted to accomplish this by developing a matched PUF pair on two chips. One could authenticate the other directly, without the need to store PUF data on third-party servers.
As an analogy, consider a sheet of paper torn in half. The torn edges are random and unique, but the pieces have a shared randomness because they fit back together perfectly along the torn edge.
While CMOS chips aren’t torn in half like paper, many are fabricated at once on a silicon wafer which is diced to separate the individual chips.
By incorporating shared randomness at the edge of two chips before they are diced to separate them, the researchers could create a twin PUF that is unique to these two chips.
“We needed to find a way to do this before the chip leaves the foundry, for added security. Once the fabricated chip enters the supply chain, we won’t know what might happen to it,” Lee explains.
Sharing randomness
To create the twin PUF, the researchers change the properties of a set of transistors fabricated along the edge of two chips, using a process called gate oxide breakdown.
Essentially, they pump high voltage into a pair of transistors by shining light with a low-cost LED until the first transistor breaks down. Because of tiny manufacturing variations, each transistor has a slightly different breakdown time. The researchers can use this unique breakdown state as the basis for a PUF.
To enable a twin PUF, the MIT researchers fabricate two pairs of transistors along the edge of two chips before they are diced to separate them. By connecting the transistors with metal layers, they create paired structures that have correlated breakdown states. In this way, they enable a unique PUF to be shared by each pair of transistors.
After shining LED light to create the PUF, they dice the chips between the transistors so there is one pair on each device, giving each separate chip a shared PUF.
“In our case, transistor breakdown has not been modeled well in many of the simulations we had, so there was a lot of uncertainty about how the process would work. Figuring out all the steps, and the order they needed to happen, to generate this shared randomness is the novelty of this work,” Lee says.
After finetuning their PUF generation process, the researchers developed a prototype pair of twin PUF chips in which the randomization was matched with more than 98 percent reliability. This would ensure the generated PUF key matches consistently, enabling secure authentication.
Because they generated this twin PUF using circuit techniques and low-cost LEDs, the process would be easier to implement at scale than other methods that are more complicated or not compatible with standard CMOS fabrication.
“In the current design, shared randomness generated by transistor breakdown is immediately converted into digital data. Future versions could preserve this shared randomness directly within the transistors, strengthening security at the most fundamental physical level of the chip,” Lee says.
“There is a rapidly increasing demand for physical-layer security for edge devices, such as between medical sensors and devices on a body, which often operate under strict energy constraints. A twin-paired PUF approach enables secure communication between nodes without the burden of heavy protocol overhead, thereby delivering both energy efficiency and strong security. This initial demonstration paves the way for innovative advancements in secure hardware design,” Chandrakasan adds.
Source: MIT News